What is a DeFi Exploit?
Exploits are (usually criminal) attempts to manipulate DeFi protocols by exploiting loopholes and logical errors in the smart contracts on which they’re run, resulting in the theft of user assets.
Given the speculative nature of blockchain tech, exploits are a major source of risk when it comes to investing in the DeFi space—even for projects that have had their smart contracts audited.
In this article, we’ll be going over the main types of DeFi exploits, some notable examples of DeFi protocols that were exploited, and what you can do to protect yourself from getting completely rekt.

The Most Common Types of DeFi Exploits
Flash loan
The majority of DeFi exploits involve something known as a flash loan.
Flash loans allow individuals to borrow large amounts of an asset without collateral as long as that loan is paid back within the same blockchain transaction.

Just as The Flash uses his superspeed for good, most individuals take advantage of flash loans for perfectly legitimate reasons (i.e. swapping collateral, self-liquidation and legitimate arbitrage opportunities).
But what happens in an alternate universe where The Flash is a supervillain?
Price oracle manipulation using flash loans
Most DeFi protocols feature in their smart contracts a piece of code called a centralized price oracle—a third-party service that retrieves external price data from asset pairs on a single decentralized exchange (DEX) such as Uniswap.

Because these protocols rely on a single DEX to feed in their price data, exploiters can manipulate the market (i.e. increase or decrease the price of a token relative to a paired token) by swapping large amounts of said token, courtesy of a flash loan, on the DEX in question.
This ultimately creates an arbitrage opportunity in which the exploiter can withdraw from the protocol a far greater amount of an asset than usually possible.
Rug pull
Less of an exploit than it is a scam, rug pulls occur when the developers of a protocol “pull the rug” on their investors and run away with their funds.

This is usually accomplished by the developers first listing their protocol token on a DEX. After attracting enough liquidity pool investment for their token pairs, the devs drain the pool, stealing the funds while driving the price of the token down to zero.
In the yield farming world, there are so many rugs—from “soft rugs” that don’t steal all users’ funds, but don’t implement anti-inflationary token measures, to “hard rugs” designed to steal every last BUSD. Check out our guide on hard rugs and exploits here: Exploits and Rug Codes
Notable DeFi Exploits
Value DeFi
Value DeFi is protocol offering a suite of DeFi services, including an automated market maker (vSwap) and a yield aggregator (vSafe).
It also apparently offers a lot of free money for potential exploiters, because it’s one of the only protocols to have been exploited three times.
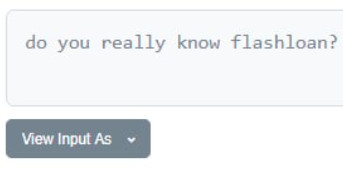
In the first attack, which occurred on November 14, 2020, an exploiter utilized a flash loan to walk away with $7 million before returning $2 million and a patronizing message to the devs (“do you really know flashloan?”).
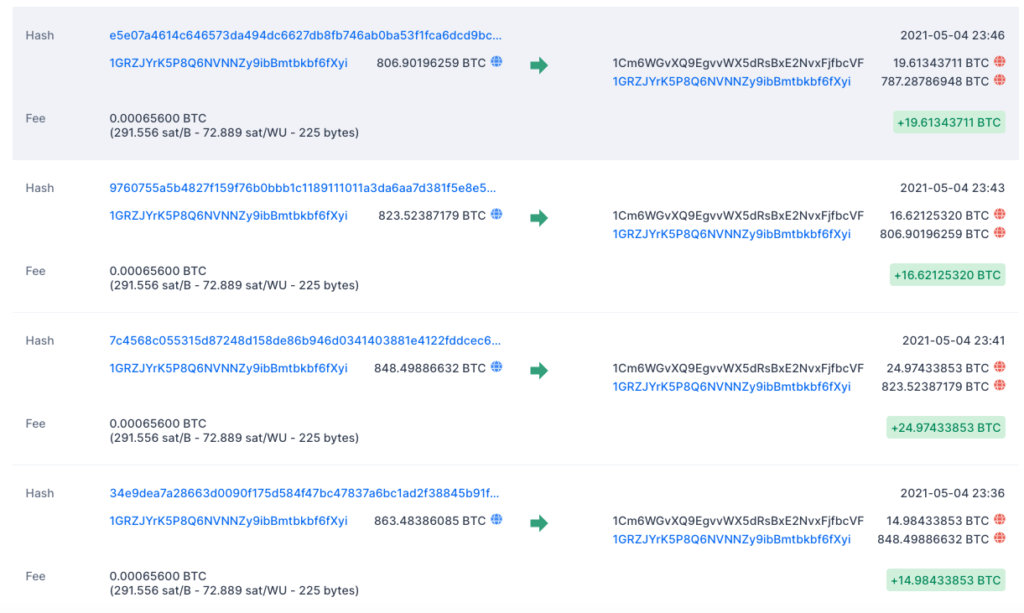
Then, on May 5, 2021, someone exploited a missing line of code that allowed them to re-initialize a pool and set themselves as the owner. They subsequently drained the stake token for vBWAP/BUSD, burned it and converted both coins into $10 million worth of BTC.
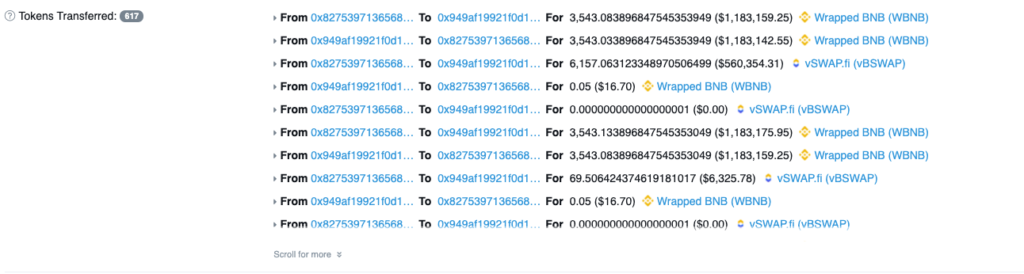
Just 3 days later, Value DeFi was exploited again. Like the second attack, the exploiter took advantage of a coding error—this time, the incorrect usage of something called a Bancor formula. This allowed the exploiter to take funds in any pool that didn’t have its liquidity split 50/50, ultimately resulting in $11 million of stolen funds.
What’s that saying they have in baseball? Three strikes and you’re out? Time will tell if Value DeFi can retain the trust of its users after this embarrassing showing at bat.
Meerkat Finance rug pull
Meerkat Finance was a fork of Alpaca.Finance—itself a fork of Yearn.Finance, a yield aggregator protocol—that operated on the Binance Smart Chain.
Just one day after its launch on March 4, 2021, it was exploited for 13 million BUSD and 73,000 BNB, totalling roughly $31 million in user funds.

While the team initially played it off as an exploit, it was later discovered that the Meerkat Finance Deployer had upgraded two of their vaults prior to the attack, giving the devs backdoor access and indicating that it was an inside job.
Interestingly, a day later, a member of the dev team named “Jamboo” surfaced on Telegram and announced that all investors would be refunded—and they were.
What was the point of it all, then? Apparently, a (very expensive) “social experiment” to test “user greed and subjectivity” in the DeFi space.
Its results were predictable and the lessons clear: don’t ape into every mouthwatering DeFi project with flashy graphics you see—especially if, like Meerkat Finance, they aren’t audited!
EasyFi
EasyFi is a lending protocol built on Polygon that holds the unenviable distinction of being victim to the largest exploit in DeFi to date.
On April 19, 2021, the attacker managed to compromise a computer used for official transactions on behalf of the protocol. They then injected a malicious version of MetaMask (a popular DeFi wallet), allowing them to steal admin keys, drain liquidity pools, and ultimately make away with roughly $6 million in stablecoins and $53 million in EASY tokens.

Harvest Finance
Harvest Finance, a yield aggregator protocol, was hit by a textbook flash loan price oracle attack targeting their FARM_USDT and FARM_USDC pools on Oct 26, 2020.

The steps they carried out were as follows (credit @valentinmihov and rekt):
- Take a $50 million USDT flash loan
- Swap $11.4 million USDC to USDT on the Curve Finance Y pool (causes USDT price to go up)
- Deposit $60.6 million USDT into vault
- Exchange $11.4 million USDT to USDC (causes USDT price to go down)
- Withdraw $61.1 million USDT from vault ($0.5 million profit)
- Rinse and repeat 32 times
- Convert to BTC (via renBTC) and withdraw; convert to ETH and withdraw via Tornado.finance, a protocol that allows for anonymous transactions
Pancake Bunny
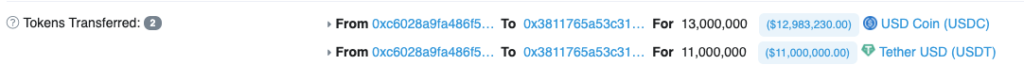
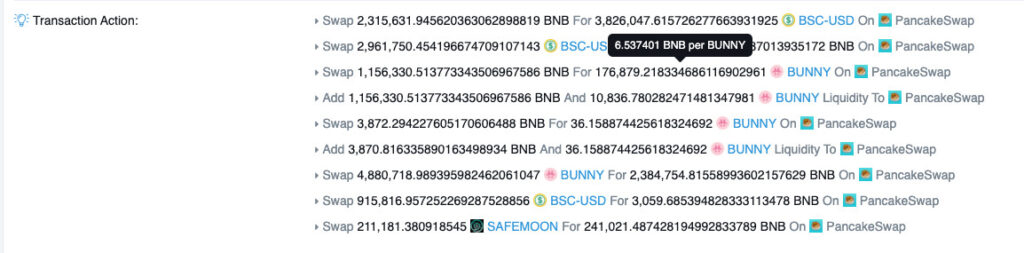
Pancake Bunny is another yield aggregator protocol that was hit by a flash loan attack on May 19, 2021, this one to the tune of $45 million.
By taking out 8 different flash loans, the exploiter was able to manipulate the price on various PancakeSwap pools and mint an unwarranted 6.97 million BUNNY tokens. These were then immediately sold for profit, causing the token’s price to crash from $146 to $6.
Other DeFi Exploits
For a comprehensive list and what to do in case you find yourself victim to a DeFi exploit, check out the following resources:
- The RugDoc Wiki
- How to emergency withdraw on the Binance Smart Chain
- How to emergency withdraw on the Polygon Network
Protecting Yourself From DeFi Exploits
So what can you do to make sure you don’t get rekt by DeFi exploits?
Well, it’s simple: do your due diligence and don’t just jump into a project because the returns are juicy.
Indeed, if the returns look too good to be true, chances are they just might be. Just look at the recent Iron Finance fiasco—no, it wasn’t an exploit and it doesn’t appear to have been a rug pull, either, but it was an example of super high APYs blinding people to the poor fundamentals behind the project.
Check to see if the project is audited. No, this doesn’t guarantee safety, but it does usually protect you from being rug pulled via backdoors and loopholes deliberately written into the smart contract.
Most importantly, keep in mind the foundational rule of investing: don’t invest what you can’t afford to lose. Blockchain and crypto is a fledgling space with all kinds of risks and unknowns. As such, the possibility of DeFi exploits will always be there, no matter how solid any given project is.