LayerFarm was a new DeFi yield farm launching on the Polygon and Binance Smart Chain networks. The project differentiated itself by having “multilevel farming worlds” and was able to attract over $450k in total value locked (TVL) just 5 hours after launching.
With zero deposit fees for many pools, users were attracted to this farm for high yields on their staked funds without the risk of losing money to deposit fees or having to wait several hours with harvest lockups.
However, there were some red flags:
- The project was rushed, announced, and began in all in the span of less than a dozen hours
- There was no time lock on the MasterChef contract
- There was novel new code involving NFTs (we’ll explain this part later)
So all-in-all, Layer.farm raised some eyebrows as they began their launch.
It wasn’t until hours after launch did they decide to pull off this clever rug…
So, How Did it Happen?
To better understand how this malicious code worked, it might be helpful to understand exactly what happens when you deposit your funds in a farm.
For example, let’s say you head on over to Beefy.finance and deposit 100 BIFI tokens into their vault. In return, you’d receive a certain amount of mooTokens (let’s say, 100) that represent your share of the vault.
Think of the mooTokens as a receipt you’d receive to prove you own your staked funds. And if Beefy wanted to take a small deposit fee, they could simply give you 4% less mooTokens (in this case, 96 total) and send the other 4 to a different address that collects the fees.
Once you’re ready to get your staked funds back, you’d simply hand over your mooTokens in exchange for your deposited funds (plus any yield the vault generated).
Sounds simple, right?
This is where Layer.farm differed.
Instead of giving mooTokens in exchange for funds, Layer.farm had a novel method of giving away an nftToken to users who staked their funds.
And whenever you’d want to take your funds back, you’d give back this nftToken… Or, that was how it was supposed to work.
You see, while Layer.farm’s smart contracts might have looked normal for the most part, there was one piece of code that was responsible for this attack:
And here are other links you might find useful before we dive in.
Now since the MasterChef contract was drained of different tokens in various liquidity pools, let’s focus on the MATIC token for an explanation by inspecting the attacker’s transactions.
Here’s the tl;dr version in 5 steps:
- The attacker called the contract’s wrap function and transferred 11,500 MATIC to the MasterChef contract.
- The NFT contract then gave 11,500 nftToken (the receipt) to the attacker in return. 4% (or, in this case, 460 nftToken) were minted in thin air and sent to the fee address.
- The attacker called the unwrap() function, which gave back the 11,500 MATIC.
- Now, this is where the extra money comes in. Since the fee address has an extra 460 nftTokens generated as a fee, the attacker simply calls the unwrap() function again to drain the 460 MATIC from the MasterChef contract.
- Rinse and repeat steps 1-4 until all the MATIC is drained from the MasterChef.
The attacker simply had to redo this process for each of the pools to steal all users’ funds. Since this is a rather novel code and might take a bit more explaining to fully understand…
Here’s the more detailed version, explained with USDT:
- First, the Attacker Contract’s Owner (ACO) sends in 10,400 USDT to the attacker contract.
- Next, the Attacker Contract (AC) calls the function setApprovalForAll on the NFT contract. This gives MasterChef approval to transfer tokens to and from the AC and AO.
- The AC calls the nftTokens are then minted to the AC.
- 4% deposit fees are given to the Fee address via minting nftTokens directly. However, no deposit fees were taken out from the AC’s original deposit.
- AC calls the “unwrap” function. The MasterChef contract, by design, checks the NFT balance of the AC and sees 10,400 nftTokens in pid 10. It then burns the nftTokens.
- In exchange, 10,400 USDT is sent back to the AC.
- The attacker repeats this process 21 times before swapping his USDT stack to PolyDoge. They then repeat the above steps again many more times, gaining more USDT and PolyDoge in the process.
- The attacker swaps PolyDoge to other tokens.
- The attacker finally unwraps his minted NFTs into the corresponding tokens and essentially drains the MasterChef contract of all users’ funds.
The Aftermath of Layer.farm’s Exploit
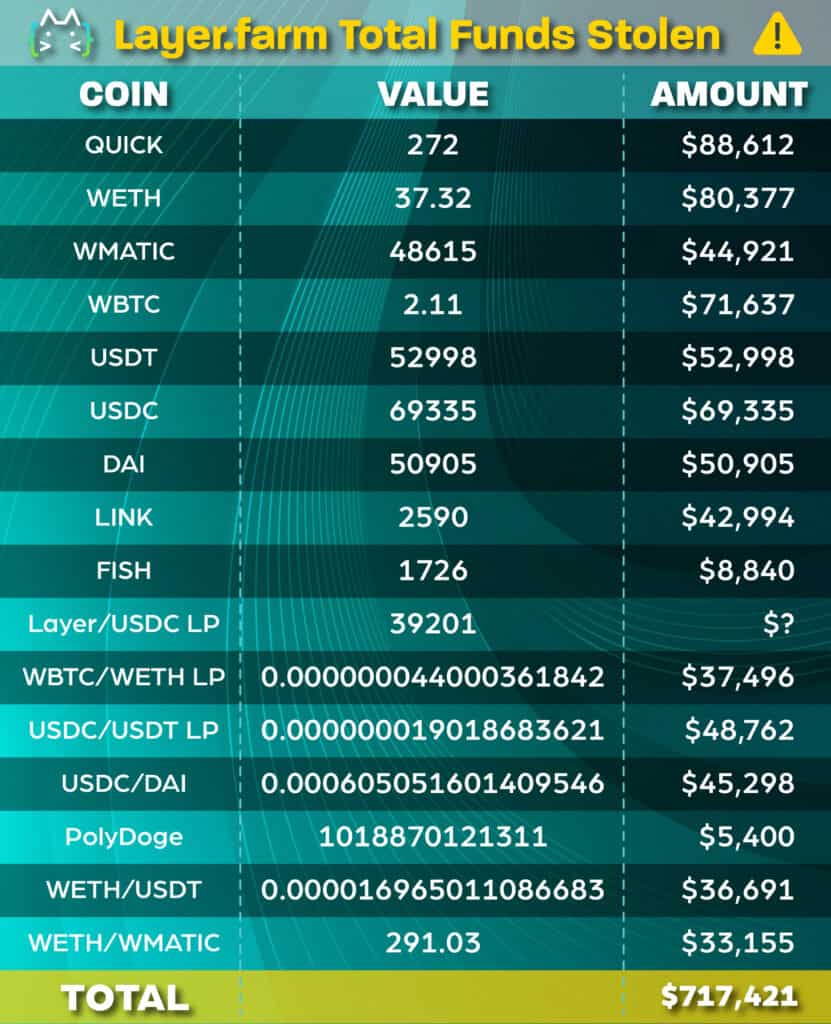
The attacker managed to steal a total of $717,421 in various crypto assets, not including their native token LAYER’s liquidity pool assets. Take a look at the chart below for a summary of what was stolen:
Do Your Own Research (DYOR)
Before aping into any yield farm, we ALWAYS advise you to do your own research and come up with a risk mitigation strategy beforehand. Never invest more than you can afford to lose, especially in newer, unestablished yield farms.
DeFi is inherently risky, risk management is key.
Layer.farm had a novel exploit never before seen in the yield farming space. Novel rugs like this are the exact reason we updated our yield farm risk ratings system so that all new farms can only receive a “some risk” rating at best.
For an overview on how we rank our risk ratings, check out the video below:
Have a burning question you want answered about DeFi or yield farms? Head on over to our Telegram channel and join our amazing community!
And as always, stay safe in the DeFi world.
Signing off,
The RugDoc Team